As biometric technology becomes increasingly important across sectors like government and banking, understanding how fingerprint scanners work is essential for selecting and implementing secure authentication systems.
“Fingerprint scanners capture an image of a person’s fingerprint and then compare it to a database of known fingerprints. This method helps verify identity by matching the captured image with stored data, commonly used in devices like smartphones and laptops. The three main types of fingerprint scanners are optical, capacitive, and ultrasonic, each offering distinct benefits in terms of accuracy and security.”
Now that we understand the basic function of fingerprint scanners, let’s dive into the different types of fingerprint scanning technologies and how they are applied in biometric systems.
How Does Fingerprint Detection Work?
Fingerprint detection is a sophisticated method that takes advantage of the unique patterns on an individual’s fingerprints. This process is crucial in areas like personal security, law enforcement, and access control. But how does this technology actually work? Let’s explore the stages involved.
Fingerprint detection uses sensors to capture the unique ridges and valleys on the skin. The data is processed into a template for future comparison, ensuring secure identification.
Dive Deeper into Fingerprint Detection
Fingerprint detection relies on a multi-step process to securely authenticate individuals. Let’s break down the steps involved and understand how each phase contributes to accurate fingerprint identification.
1. Fingerprint Capture
The first step in fingerprint detection involves capturing an image of the fingerprint using various types of sensors:
Optical Scanners
These scanners use light to capture a digital photograph of the fingerprint. The light-sensitive chip processes the ridges and valleys of the fingerprint, converting them into binary data (1s and 0s) for digital representation.
Capacitive Scanners
Capacitive scanners work by detecting the electrical charges created by the ridges and valleys of the fingerprint. When a finger touches the scanner, the ridges create a higher contact area, influencing the charge, while the valleys have a lesser effect.
Ultrasound Scanners
Ultrasound scanners use sound waves to capture a 3D image of the fingerprint, allowing for accurate scans even without direct contact with the scanner.
Thermal Scanners
These scanners measure temperature differences between the ridges and valleys, generating an image based on heat signatures.
2. Feature Extraction
Once the fingerprint is captured, the system extracts unique features like ridge endings and bifurcations. These are the points where ridges split. This step helps transform the raw image into a unique template that holds the biometric data.
3. Template Creation
The features extracted from the fingerprint are then encoded into a mathematical model or algorithm. This template does not store the image itself but rather a binary code that can be used for comparisons in the future.
4. Matching Process
During authentication, the system compares the newly captured fingerprint against stored templates using pattern-matching algorithms. The matching process analyzes similarities and differences to identify if the templates match.
Minutiae-based Matching
This method focuses on specific fingerprint points, such as ridge endings and bifurcations, to compare the captured fingerprint with stored templates.
5. Authentication Decision
Once a match is identified, access is granted. If no match is found, access is denied. The system is often designed to accommodate small variations, such as dirt on the fingerprint or minor cuts, ensuring accuracy even in less-than-ideal conditions.
How Accurate is Fingerprint Scanning?
In today’s digital age, fingerprint scanning has become a common method for identification and authentication.
Fingerprint scanners today can achieve over 99% accuracy under optimal conditions, making them highly reliable for security purposes.

Let me delve into the accuracy of fingerprint scanning technology and the factors that influence its performance.
How Accurate is Fingerprint Scanning?
Fingerprint scanning technology has reached impressive levels of accuracy, with modern systems performing at over 99% accuracy when conditions are ideal.
Diving Deeper into Fingerprint Scanner Accuracy
Fingerprint scanners are widely used in various applications, from unlocking smartphones to securing sensitive facilities. Understanding their accuracy involves looking at different performance metrics and influencing factors.
Accuracy Levels
Fingerprint scanners generally exhibit high accuracy rates, which can be summarized as follows:
| Test Type | Accuracy Rate |
| Single-finger tests | 98.6% |
| Two-finger tests | 99.6% |
| Four or more fingers | 99.9% |
These statistics are supported by research from the National Institute of Standards and Technology (NIST), which found that the best systems achieve these high accuracy rates.
False Positive Rates
The false positive rate of fingerprint scanners is exceptionally low, around 0.01%. This means that only one in 10,000 scans may incorrectly identify a fingerprint, ensuring a high level of reliability.
Factors Influencing Accuracy
Several factors can impact the accuracy of fingerprint scanning:
Quality of Fingerprints: Clear and complete fingerprint images are crucial for accurate identification. Poor quality images, caused by moisture, dirt, or partial prints, can lead to lower identification rates.
Number of Fingers Used: Scanning multiple fingers increases the likelihood of a correct match. Systems that utilize more fingers typically achieve higher accuracy.
Scanner Technology: Different types of fingerprint scanners—such as optical, capacitive, and ultrasound—have varying levels of accuracy based on their design and technology.
Limitations and Considerations
While fingerprint scanners are highly accurate, there are some limitations to consider:
Miss Rate: Modern fingerprint scanners do not yet meet the ideal standards set by NIST, which aims for a miss rate of 0.00001% (one error in every 100,000 scans).
Vulnerabilities: Although rare, it is possible to bypass scanners using fabricated fingerprints. This requires significant effort and skill, making it a less common threat.
Real-World Example
In a study conducted by NIST, the best fingerprint scanning systems achieved up to 99.9% accuracy when multiple fingers were used. This high level of accuracy demonstrates the reliability of fingerprint scanning technology in various applications, from security systems to personal devices.
What Influences the Accuracy of Fingerprint Scanning?
Several key factors influence the accuracy of fingerprint scanning technology:
Quality of Fingerprint Images
High-quality fingerprint images are essential for accurate identification. Factors such as moisture, dirt, and partial prints can degrade image quality, leading to lower accuracy rates.
Number of Fingerprints Scanned
Scanning multiple fingers increases the reliability of the identification process. Systems that use more fingerprints tend to have higher accuracy rates, as there is more data to verify a match.
Type of Scanner Technology
Different scanner technologies offer varying levels of accuracy:
| Scanner Type | Description |
| Optical | Uses light to capture fingerprint images |
| Capacitive | Uses electrical signals to capture images |
| Ultrasound | Uses sound waves to create detailed images |
Each type has its strengths and weaknesses, influencing overall accuracy. For instance, ultrasound scanners can capture more detailed images, improving accuracy in challenging conditions.
What Are the Future Trends in Fingerprint Scanning Accuracy?
Fingerprint scanning technology continues to evolve, with future trends focusing on enhancing accuracy and security.
Improved Imaging Technologies
Advancements in imaging technologies will lead to even clearer and more detailed fingerprint images. Enhanced sensors and better algorithms will reduce errors and increase the reliability of fingerprint scanners.
Integration with AI
Artificial intelligence and machine learning algorithms will improve the analysis and matching processes. These technologies can reduce false positives and negatives by learning from vast amounts of fingerprint data, making scans more accurate over time.
Enhanced Security Features
Future fingerprint scanners will incorporate advanced security features to prevent spoofing and unauthorized access. Techniques such as liveness detection and multi-factor authentication will further enhance the security and accuracy of fingerprint scanning systems.
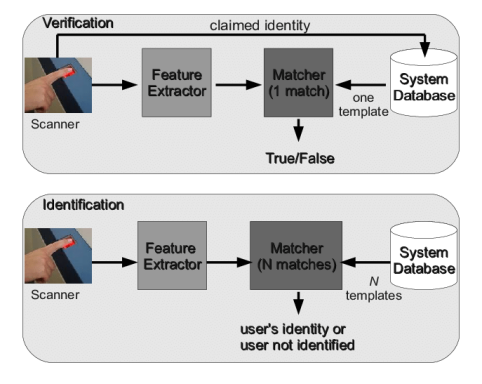
How Does Fingerprint Verification Work?
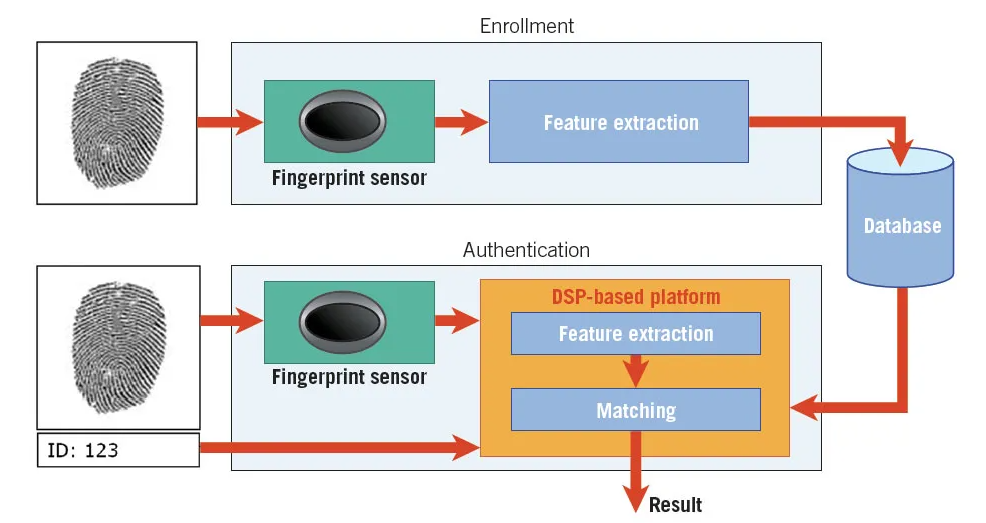
Fingerprint verification is a biometric process that uses the unique patterns found in an individual’s fingerprints to verify their identity. It is commonly used in security systems and devices. Here’s a closer look at how the entire process works, from initial enrollment to final authentication.
Fingerprint verification works by capturing unique fingerprint data, processing it into a biometric template, and comparing it during authentication. The system uses sophisticated algorithms to ensure high accuracy.
Dive Deeper into Fingerprint Verification
Fingerprint verification relies on the uniqueness of each person’s fingerprint. But how exactly does the system identify and verify a fingerprint? Let’s break it down into its core steps.
1. Enrollment Process
The first stage in fingerprint verification is enrollment, where the system collects and stores the user’s fingerprint data.
Fingerprint Scanning
The user places one or more fingers on a scanner. This could be an optical, capacitive, ultrasound, or thermal scanner. Each type of scanner uses different methods to capture the fingerprint, focusing on the ridges and valleys that form the unique patterns.
Data Processing
Once the fingerprint is captured, the system processes the image to extract specific features such as minutiae points (ridge endings, bifurcations) and overall patterns. These features are then converted into a biometric template, a digital representation of the fingerprint that is used for comparison during verification.
2. Data Storage
The processed fingerprint data is stored securely in an encrypted format. The encrypted data ensures that even if someone gains unauthorized access to the system, they cannot exploit the raw biometric information.
3. Verification Process
When the user tries to authenticate their identity, the following steps occur:
Fingerprint Capture
The user places their finger on the scanner again. The system captures the new fingerprint image for comparison.
Feature Extraction
Like in the enrollment process, the system processes this new fingerprint to extract its distinct features. These features are converted into a new biometric template.
Matching
The system compares the new fingerprint template against the stored templates. Several techniques are used for matching:
- Minutiae-based Matching: This method compares specific points in the fingerprint, like ridge endings and bifurcations, that make each fingerprint unique.
- Pattern Matching: Some systems may analyze the overall patterns in the fingerprint rather than focusing solely on minutiae.
4. Decision Making
Once the comparison is made, the system evaluates whether there is a match. The system uses a threshold to determine if the similarity score between the captured fingerprint and the stored template is sufficient. If the score exceeds the threshold, access is granted; otherwise, it is denied.
The accuracy of this process can be 99% or higher under optimal conditions, with minimal risk of false positives or negatives.
What is a Fingerprint Scanner Used For?
Fingerprint scanners play a crucial role in today’s world, widely applied across various fields to enhance security and convenience.
Fingerprint scanners are primarily used for security control, law enforcement, biometric identification, healthcare, financial services, and personal convenience.
I remember the first time I unlocked my phone with my fingerprint. The ease and speed made me fascinated with fingerprint technology, prompting me to explore its other applications.
Fingerprint Scanners in Security and Access Control
Fingerprint scanners are extensively used in security and access control to ensure that only authorized personnel can enter specific areas.
In security and access control, fingerprint scanners are used for device unlocking and controlling access permissions, thereby enhancing overall security.
Device Unlocking
Fingerprint scanners are commonly found in smartphones and other electronic devices. They allow for quick and secure device unlocking, reducing the risk of password breaches.
| Application Scenario | Specific Use |
| Smartphones | Unlocking devices, verifying payments |
| Office Equipment | Logging into computers, protecting sensitive information |
| Access Control Systems | Controlling entry to office buildings or restricted areas |
Physical Access Control
In businesses and institutions, fingerprint scanners are used to manage employee access to specific areas, ensuring that only authorized individuals can access important locations.
Fingerprint Scanners in Law Enforcement and Criminal Justice
Law enforcement agencies use fingerprint scanners for identifying suspects and conducting background checks, improving efficiency and accuracy.
Law enforcement agencies use fingerprint scanners to identify suspects and perform background checks, enhancing the reliability of the justice system.
Criminal Identification
Police use fingerprint scanners to compare fingerprints found at crime scenes with those in databases, speeding up case resolution.
Background Checks
During the hiring process, especially for security-sensitive positions, fingerprint scanners help perform accurate background checks to ensure candidate reliability.
Fingerprint Scanners in Biometric Identification Systems
Fingerprint scanners play a significant role in border control and voter identification, ensuring accurate identity verification and system security.
In biometric identification systems, fingerprint scanners are used for border control and voter identification, preventing fraud.
Border Control
Travelers use fingerprint scanners at immigration checkpoints to verify their identities against government databases, ensuring the authenticity of their entry.
Voter Identification
Some voting systems implement fingerprint verification to prevent election fraud and maintain the integrity of the electoral process.
Fingerprint Scanners in Healthcare and Medical Applications
Hospitals use fingerprint scanners to accurately identify patients, ensuring that medical records are correctly matched to the right individual, which is vital for patient safety.
In the healthcare field, fingerprint scanners are used for patient identification to prevent medical errors and improve care quality.
Patient Identification
By scanning fingerprints, hospitals can quickly and accurately identify patients, ensuring that medical records correspond to the correct individual.
Fingerprint Scanners in Financial Services
Banks and financial institutions adopt fingerprint scanners for transaction verification, enhancing the security and convenience of financial operations.
Financial institutions use fingerprint scanners for transaction verification, safeguarding customer funds and simplifying processes.
Banking Transactions
Customers can authorize payments or access their accounts using fingerprint scanners, avoiding the hassle and risks associated with traditional passwords.
Fingerprint Scanners for Personal Use and Convenience
Fingerprint scanners offer various conveniences in personal life, such as digital signatures and secure login for mobile applications.
Individual users utilize fingerprint scanners for digital signatures and secure logins, enhancing daily convenience.
Digital Signature Verification
Fingerprint scanners are used to verify electronic document signatures, ensuring the authenticity and security of signed files.
Mobile Applications
Many apps use fingerprint scanners for secure logins, such as password managers and encrypted file storage, protecting user privacy.
Fingerprint Scanners in Research and Development
Fingerprint scanners are essential in biometric research, helping improve algorithms and enhance overall system accuracy and security.
Researchers use fingerprint scanners in biometric studies to optimize algorithms and increase system security.
Biometric Research
Fingerprint scanners enable researchers to collect extensive data, analyze fingerprint characteristics, and refine recognition algorithms to improve accuracy.
Technological Innovation
Ongoing research and development drive advancements in fingerprint scanning technology, expanding its applications across more fields.
Types of Fingerprint Sensors in Mobile Devices
Fingerprint sensors in mobile devices come in various types, each utilizing unique technologies to capture and process fingerprint data effectively.
There are primarily four types of fingerprint sensors used in mobile devices: optical, capacitive, ultrasonic, and thermal sensors.
When I first explored different smartphones, I was amazed by the variety of fingerprint sensors and how each type offered distinct advantages.

Optical Fingerprint Sensors
Optical fingerprint sensors use light to create a digital image of a fingerprint. When a finger touches the sensor, it illuminates the fingerprint, and a camera captures the reflected light to form an image based on the fingerprint’s ridges and valleys.
| Feature | Description |
| Cost | Generally affordable and easy to implement |
| Security | Susceptible to spoofing with high-quality replicas |
| Performance | May struggle with dirty or wet fingers |
Capacitive Fingerprint Sensors
Capacitive sensors detect electrical charge differences between the ridges and valleys of a fingerprint. When a finger touches the sensor, it alters the charge stored in capacitors beneath the surface, creating a detailed fingerprint map.
| Feature | Description |
| Security | More secure than optical sensors, harder to spoof |
| Functionality | Supports gesture recognition for enhanced user interaction |
| Limitations | Requires direct skin contact, may not work well with gloves |
Ultrasonic Fingerprint Sensors
Ultrasonic sensors use sound waves to capture fingerprint details. When a finger is placed on the sensor, ultrasonic pulses are emitted and bounce back from the fingerprint’s surface, creating a 3D map of its unique features.
| Feature | Description |
| Security | Less susceptible to spoofing compared to optical sensors |
| Integration | Can be placed under glass screens without compromising security |
| Cost | Typically more expensive than optical and capacitive sensors |
Thermal Fingerprint Sensors
Thermal sensors detect heat differences between the ridges and valleys of a fingerprint. When a finger touches the sensor, it creates a thermal pattern that can be analyzed to identify the fingerprint.
| Feature | Description |
| Security | Enhanced security by relying on heat patterns |
| Usage | Less common in current smartphones, emerging technology |
| Advantages | Can provide additional layers of security by detecting live skin |
What are the Problems with Fingerprint Biometrics?
Fingerprint biometrics are widely used for secure authentication, but they come with several significant issues that can compromise security and user privacy.
Fingerprint biometrics face challenges such as spoofing attacks, false acceptance and rejection rates, data handling vulnerabilities, technical flaws, physical attacks, and privacy concerns.
I remember the first time I used my fingerprint to unlock my phone. It felt secure, but I soon wondered about the potential vulnerabilities of such biometric systems.

Spoofing Attacks in Fingerprint Biometrics
Spoofing attacks are a major concern in fingerprint biometrics, allowing unauthorized access by deceiving the system.
Spoofing attacks involve creating fake fingerprints or manipulating existing ones to bypass security measures, posing significant threats to fingerprint biometric systems.
Residual Fingerprint Attack
Residual fingerprint attacks occur when attackers collect fingerprints left on surfaces and reproduce them using materials like gelatin or silicone.
| Attack Type | Description |
| Residual Fingerprint Attack | Reproducing fingerprints from surfaces using molds |
| Substitution and Modification Attacks | Using artificial fingerprints made from materials such as latex or wax |
| Gummy Bear Attack | Utilizing fake fingerprints made from gummy bears to trick the system |
Mitigation Strategies
To combat spoofing, developers implement liveness detection and use multi-factor authentication to ensure the fingerprint belongs to a real person.
False Acceptance and Rejection Rates
Fingerprint systems sometimes incorrectly accept unauthorized fingerprints or reject legitimate ones, affecting reliability.
False Acceptance Rate (FAR) and False Rejection Rate (FRR) are critical metrics that highlight the accuracy and reliability issues in fingerprint biometric systems.
False Acceptance Rate (FAR)
FAR occurs when the system mistakenly accepts a fingerprint that does not belong to an authorized user, potentially leading to unauthorized access.
| Metric | Description |
| FAR | The rate at which unauthorized fingerprints are accepted |
| FRR | The rate at which authorized fingerprints are rejected |
| Balance | Achieving a low FAR and FRR simultaneously is challenging |
False Rejection Rate (FRR)
FRR happens when the system fails to recognize a legitimate user’s fingerprint, causing inconvenience and access issues.
Balancing FAR and FRR
Designing systems to minimize both FAR and FRR is essential but often difficult, requiring sophisticated algorithms and high-quality sensors.
Vulnerabilities in Data Handling
The security of fingerprint biometric data is crucial, as breaches can have lasting consequences.
Data breaches and network-based attacks pose significant risks to fingerprint biometric systems, as compromised data cannot be easily changed or protected once stolen.
Data Breaches
Unlike passwords, biometric data like fingerprints cannot be altered. If stolen, attackers can misuse the data indefinitely.
Network-Based Attacks
Fingerprint systems are vulnerable to attacks during data transmission, such as session hijacking and privilege escalation, which can compromise the integrity of biometric data.
| Vulnerability Type | Description |
| Data Breaches | Unauthorized access to stored fingerprint data |
| Network-Based Attacks | Attacks targeting data during transmission |
| Long-Term Exploitation | Biometric data cannot be changed if compromised |
Protecting Biometric Data
Implementing robust encryption and secure data storage protocols can help protect fingerprint data from breaches and attacks.
Technical Vulnerabilities
Fingerprint biometric systems can have inherent technical flaws that attackers exploit.
Technical vulnerabilities like the BrutePrint attack and sensor flaws can undermine the security of fingerprint biometric systems, allowing attackers to bypass authentication mechanisms.
BrutePrint Attack
BrutePrint attacks exploit weaknesses in fingerprint authentication frameworks, enabling attackers to perform brute force attempts without triggering security measures.
Sensor Flaws
Research has revealed vulnerabilities in fingerprint sensors, particularly in laptops, which can allow attackers to bypass authentication mechanisms through poor security implementations.
| Technical Vulnerability | Description |
| BrutePrint Attack | Exploiting authentication framework weaknesses |
| Sensor Flaws | Vulnerabilities in fingerprint sensors that can be bypassed |
Enhancing Technical Security
Regular updates and rigorous testing of fingerprint sensors can help identify and fix technical vulnerabilities, strengthening overall security.
Physical Attacks
Physical manipulation of biometric devices can lead to unauthorized access through hardware exploitation or fingerprint replicas.
Physical attacks on biometric systems involve tampering with devices or using physical replicas of fingerprints to gain unauthorized access, posing serious security threats.
Device Tampering
Attackers may physically alter biometric terminals or devices to weaken their security and facilitate unauthorized access.
Using Fingerprint Replicas
Creating and using physical replicas of fingerprints can deceive biometric systems, especially those without robust liveness detection.
| Physical Attack Type | Description |
| Device Tampering | Manipulating hardware to bypass security measures |
| Fingerprint Replicas | Using fake fingerprints to deceive biometric systems |
Strengthening Physical Security
Implementing tamper-evident hardware and enhancing liveness detection can mitigate the risks of physical attacks on biometric devices.
Privacy Concerns
The use of fingerprint biometrics raises significant privacy issues related to data collection, storage, and potential misuse.
Fingerprint biometric systems can lead to privacy infringements if biometric data is improperly handled or misused, emphasizing the need for stringent privacy protections.
Data Profiling
Biometric systems can collect extensive data about individuals, potentially leading to profiling and misuse if not properly secured.
Misuse of Personal Data
Without adequate security measures, biometric data can be accessed and used for purposes beyond authentication, infringing on personal privacy.
| Privacy Issue | Description |
| Data Profiling | Collecting and potentially misusing extensive biometric data |
| Misuse of Personal Data | Unauthorized use of biometric data for unintended purposes |
Ensuring Privacy Protection
Adopting strict data governance policies and ensuring transparent data handling practices are essential to protect user privacy in biometric systems.
Conclusion
Fingerprint scanners play a crucial role in biometric authentication, offering robust security across industries. By understanding the underlying technologies and their applications, biometric solution providers can make informed decisions for securing systems and enhancing user experiences.



